Cách lấy tài khoản google driver dung lượng k giới hạn
×
[PR]上記の広告は3ヶ月以上新規記事投稿のないブログに表示されています。新しい記事を書く事で広告が消えます。
Cách lấy tài khoản google driver dung lượng k giới hạn
-
Như mọi người đều biết về google driver, một sản phẩm lưu trữ đám mây do Google cung cấp, được rất nhiều người sử dụng đến, chỉ cần bạn có tài khoản email là bạn được miễn phí ngay 15GB không gian để lưu trữ, với những người ít dữ liệu thì chừng đó dung lượng là rất ok, nhưng với dân thiết kế hoặc bạn cần lưu trữ dữ liệu lớn thì chừng đó là không đủ. Chính vị vậy hôm nay mình chia sẻ bạn cách để lấy dung lượng không giới hạn từ google driver.
Các doanh nghiệp giáo dục sẽ được Google cung cấp dịch vụ lưu trữ không giới hạn. Thay vì 15Gb lưu trữ như thông thường. Google Drive có gói lưu trữ không giới hạn tặng cho học sinh, sinh viên và giáo viên.Đây là hành động đầy tính nhân văn của Google. Họ cho rằng đó là cách tốt nhất để khuyến khích việc học. Google muốn tạo không gian và điều kiện lưu trữ tài liệu học thoải mái và tiện lợi nhất.Mình sẽ chỉ bạn cách tạo tài khoản Google Drive không giới hạn. Trước hết, bạn phải có một Email học tập dạng edu được Google công nhận.
1. Tạo tài khoản CCCApplyMình chọn một dịch vụ giáo dục tại Canada để đăng ký cho uy tín. Bạn vào trang web Canada College bên dưới đến đăng ký tài khoản.Click theo link này: https://home.cccapply.org/
Chọn Canada coledge - Chọn Apply - Chọn tiếp Apply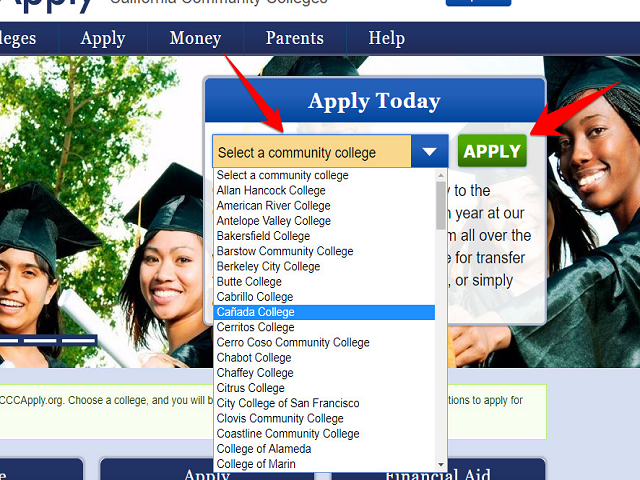 Tiếp theo
Tiếp theo

Ấn Create an Account để tạo tài khoản mới.
Tiếp tục bạn chọn Begin Creating an Account để nó mở trang đăng ký mới.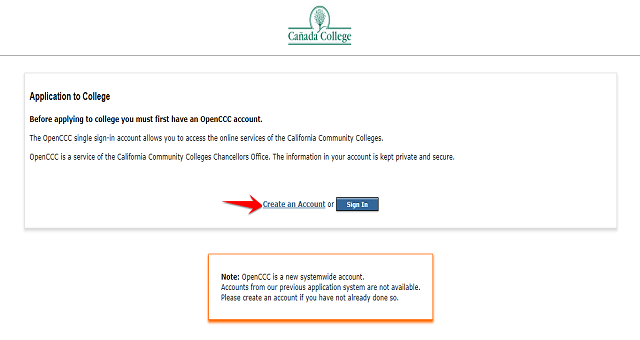
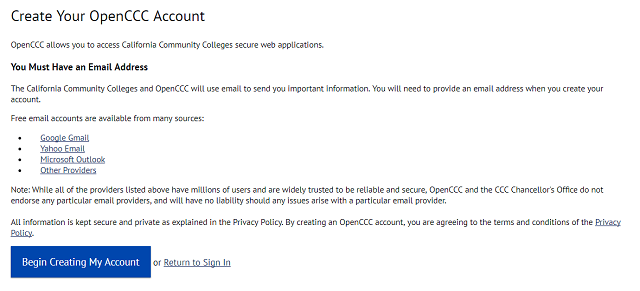
Bạn sẽ được yêu cầu điền thông tin đăng ký như thế này.
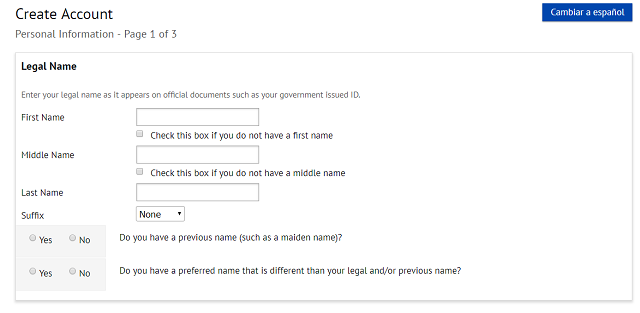
Chúng ta cần giả mạo thông tin của một người Canada để điền. Bạn vào trang web giả mạo thông tin mình để dưới đây. Nó sẽ cho bạn một thông tin giả của công dân nước ngoài.
Click theo link này: https://www.fakenamegenerator.com/
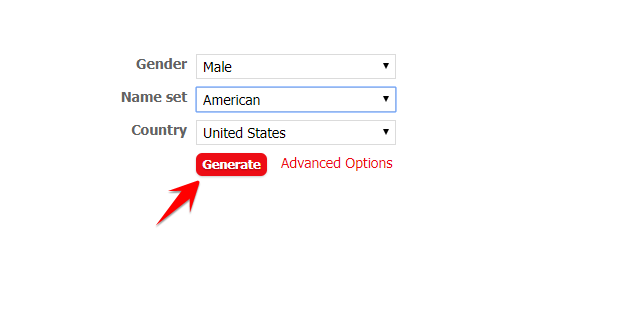
Ấn vào Generate để tạo thông tin.
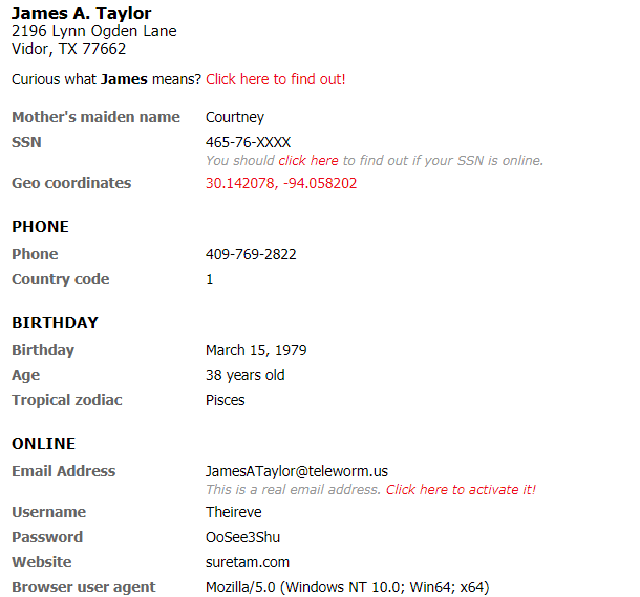
Bạn chỉ cần copy thông tin ở đây và điền vào form đăng ký kia thôi. Nhớ check theo ảnh dưới đây để hợp lệ thông tin nhé.
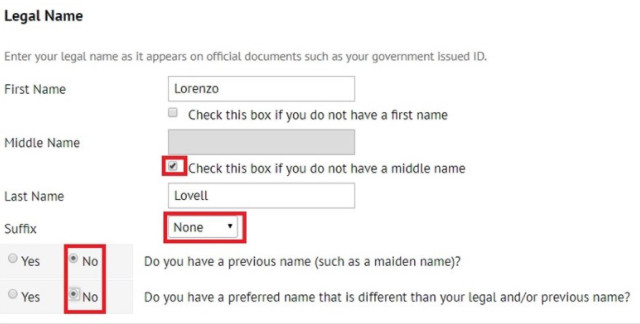
Ở phần năm sinh, bạn nhập sao cho lớn tuổi một chút để có độ tin tưởng, mình nhập 1989.
Ở phần Social bạn tích chọn vào Social Security Number.
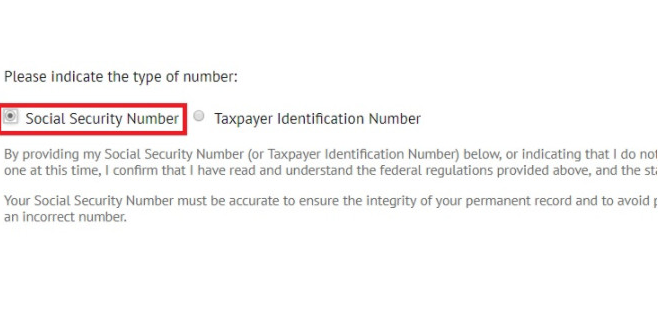 Lấy số SSNBạn cần một số SSN của công dân, số này cũng giống như số chứng minh nhân dân của Mỹ vậy. Hãy chọn một trong 2 địa chỉ dưới đây để tạo giả số SSN.Click theo link này: https://www.ssn-verify.com/generateẤn vào SSN Generate để tạo SSN giả.
Lấy số SSNBạn cần một số SSN của công dân, số này cũng giống như số chứng minh nhân dân của Mỹ vậy. Hãy chọn một trong 2 địa chỉ dưới đây để tạo giả số SSN.Click theo link này: https://www.ssn-verify.com/generateẤn vào SSN Generate để tạo SSN giả.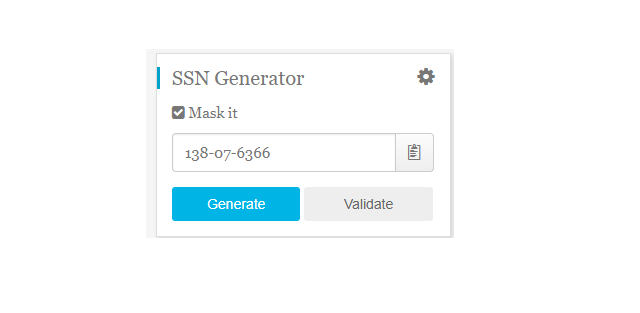 Điền số SSN đã tạo vào ô Social Security Number của Form đăng ký. Bạn gõ dính liên và không có dấu gạch giữa nha. Ví dụ như hình trên thì mình sẽ gõ 138076366. Điền xong thì ấn Continue để đăng ký.
Điền số SSN đã tạo vào ô Social Security Number của Form đăng ký. Bạn gõ dính liên và không có dấu gạch giữa nha. Ví dụ như hình trên thì mình sẽ gõ 138076366. Điền xong thì ấn Continue để đăng ký.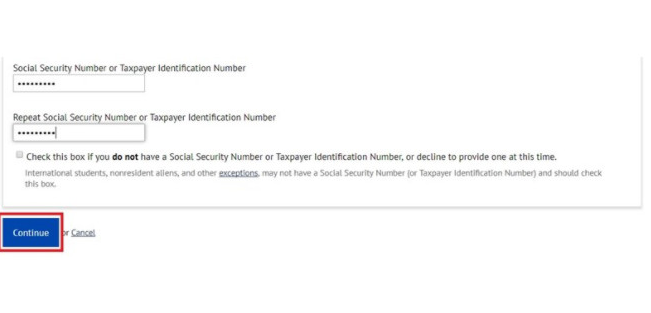 Bạn sẽ được chuyển sang trang điền Email. Hãy điền vào Gmail mà bạn hay dùng để sau này dễ nhớ mà đăng nhập.
Bạn sẽ được chuyển sang trang điền Email. Hãy điền vào Gmail mà bạn hay dùng để sau này dễ nhớ mà đăng nhập.
Ở mục điền số điện thoại, bạn hãy tạo giả một số điện thoại tại đây để điền vào. Khi vào web tạo số điện thoại, nhìn qua bên phải sẽ có bảng tạo số điện thoại. Mình chọn State là CA(Canada) cho dễ qua mặt.Copy số điện thoại vào ô Main Telephone Number.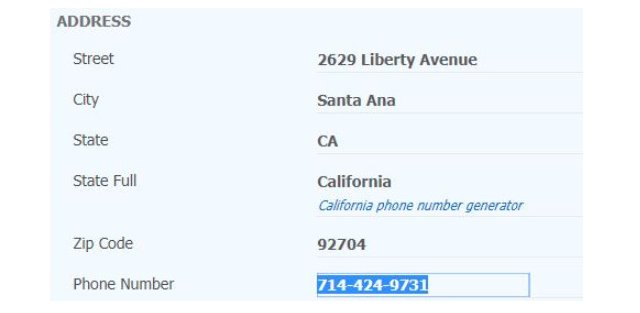 Tiếp theo bạn sẽ giả mạo địa chỉClick theo link này: https://www.fakeaddressgenerator.com/Random_Address/US_California
Tiếp theo bạn sẽ giả mạo địa chỉClick theo link này: https://www.fakeaddressgenerator.com/Random_Address/US_California
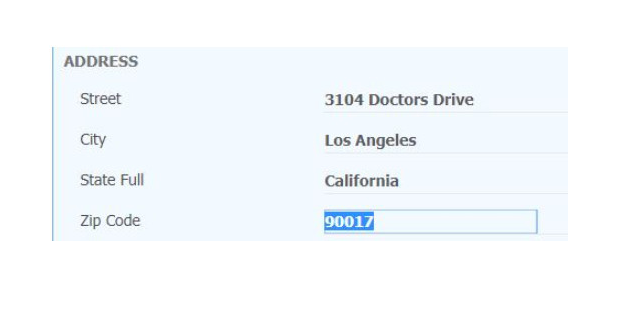
Sao chép thông tin địa chỉ và dán vào mục Permanent Address như hình dưới đây. Gồm Street Address, City, State ZIP Code. Nhớ tích chọn I have verified the address entered is correct.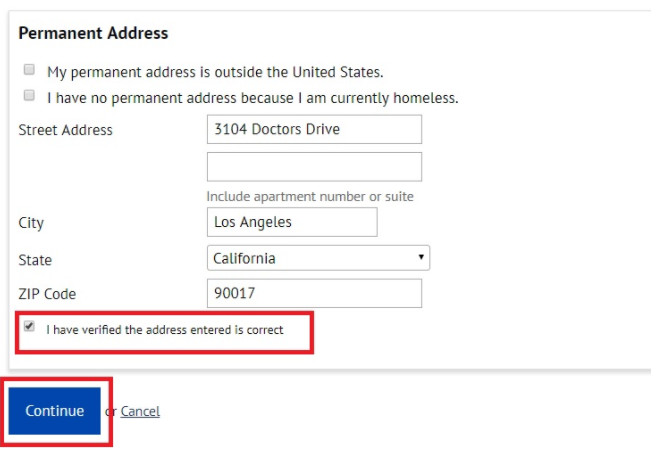 Bây giờ bạn sẽ đến giao diện Create an Account và bạn cần nhập tên tài khoản, mật khẩu gồm 7 đến 20 ký tự có cả số và chữ, câu hỏi bảo mật, mã PIN. Khi điền xong bạn nhấn Creat My Account.
Bây giờ bạn sẽ đến giao diện Create an Account và bạn cần nhập tên tài khoản, mật khẩu gồm 7 đến 20 ký tự có cả số và chữ, câu hỏi bảo mật, mã PIN. Khi điền xong bạn nhấn Creat My Account.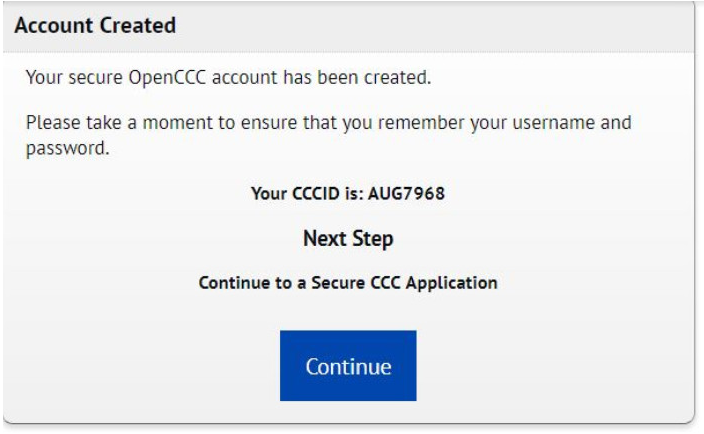 Tài khoản được tạo hoàn tất, bbạn sẽ được cấp thông tin CCCID cá nhân như ảnh trên. Ấn Continue để tiếp tục.
Tài khoản được tạo hoàn tất, bbạn sẽ được cấp thông tin CCCID cá nhân như ảnh trên. Ấn Continue để tiếp tục.
2. Xin vào trường đại học
Truy cập lại địa chỉ https://home.cccapply.org/ và chọn Canada College rồi ấn Apply như lúc đầu. Lần này chúng ta không chọn Create an account nữa mà chọn Sign in.
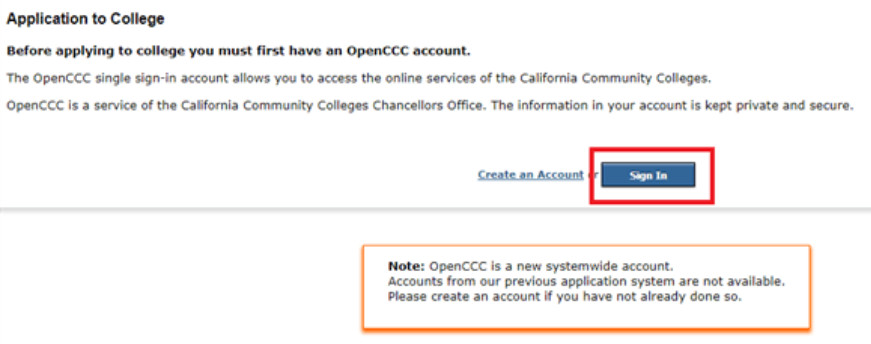 Tiếp theo chọn Start a New Application để cập nhật thông tin cá nhân.
Tiếp theo chọn Start a New Application để cập nhật thông tin cá nhân.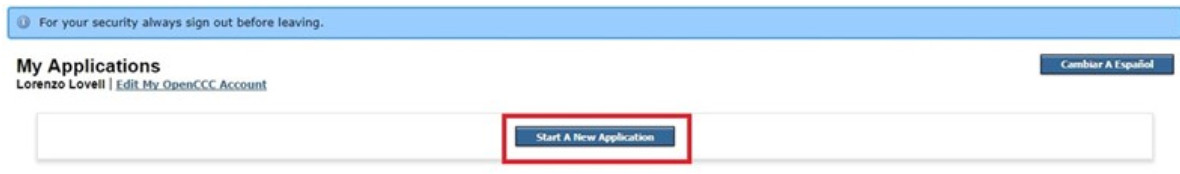 Ở phần Enrollment Infomation bạn điền như trong ảnh dưới đây và ấn Continue.
Ở phần Enrollment Infomation bạn điền như trong ảnh dưới đây và ấn Continue.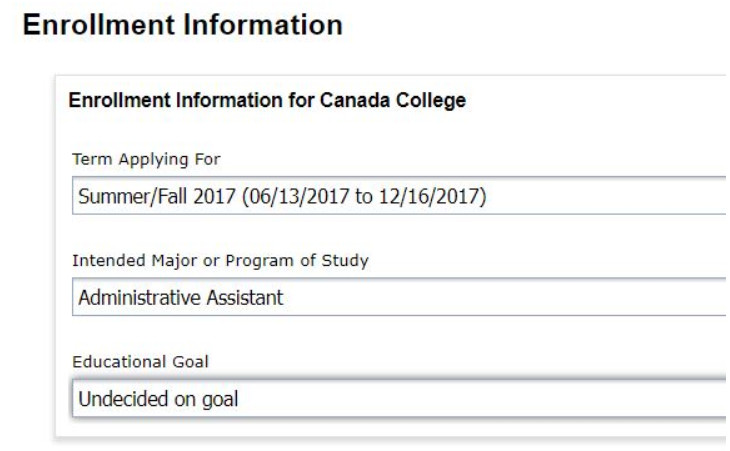 Tại mục Account/Mailing Infomation, bạn chọn My mailing address is the same as the Permanent Address in my OpenCCC Account above trongphần Current Mailing Address, rồi ấn Continue.
Tại mục Account/Mailing Infomation, bạn chọn My mailing address is the same as the Permanent Address in my OpenCCC Account above trongphần Current Mailing Address, rồi ấn Continue.
 Điền thông tin như trong ảnh tại phần Personal Information. Mọi việc còn lại các bạn chọn và điền giống theo ảnh là được.
Điền thông tin như trong ảnh tại phần Personal Information. Mọi việc còn lại các bạn chọn và điền giống theo ảnh là được.
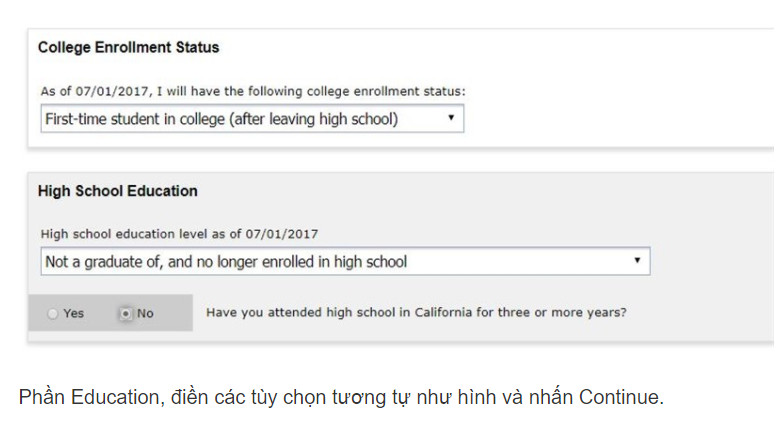
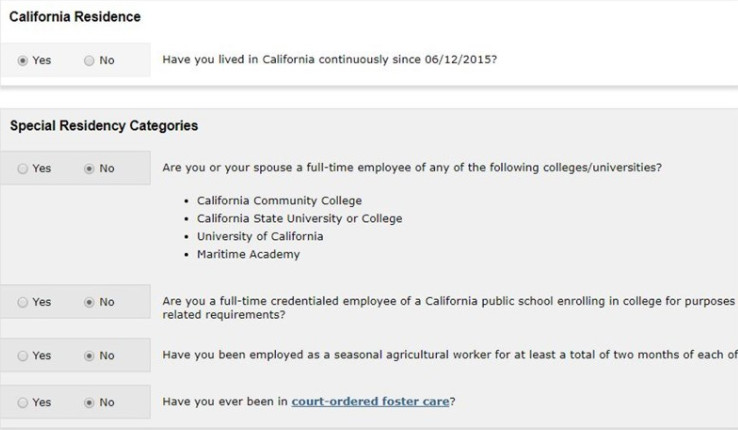
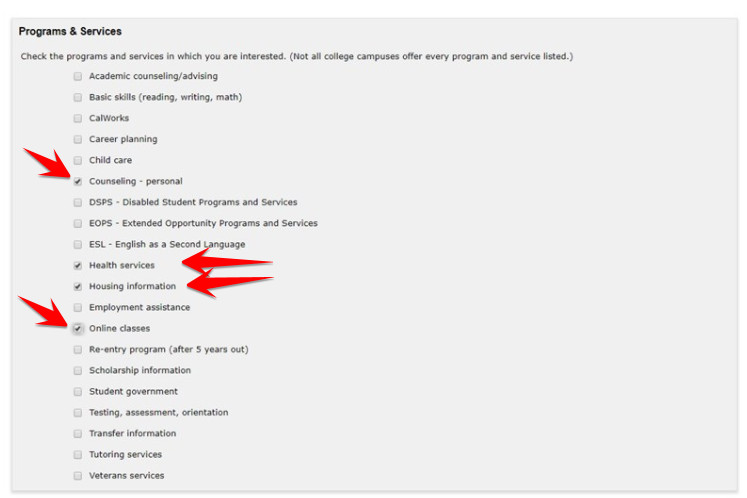
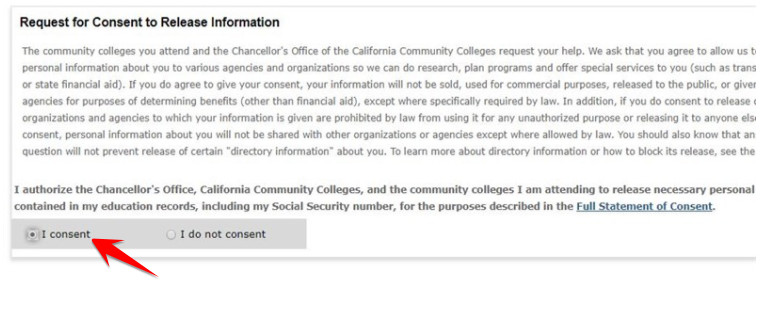
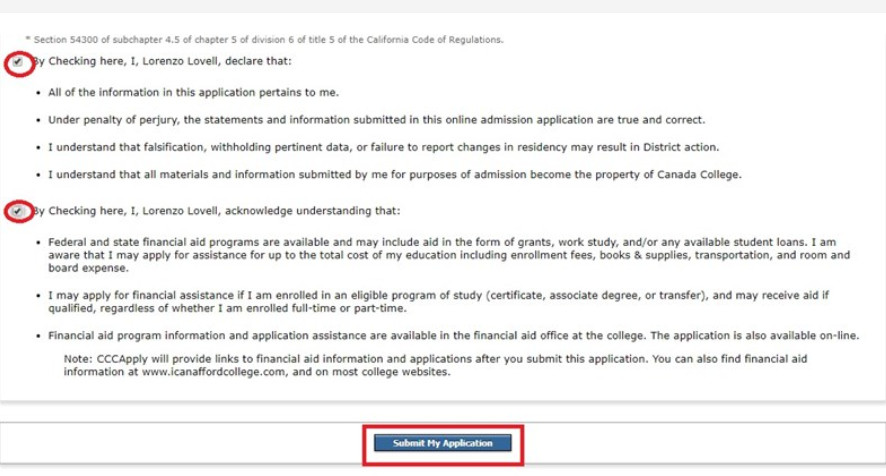
Nhớ chọn None Apply to me. Tiếp tục check như trong ảnh dưới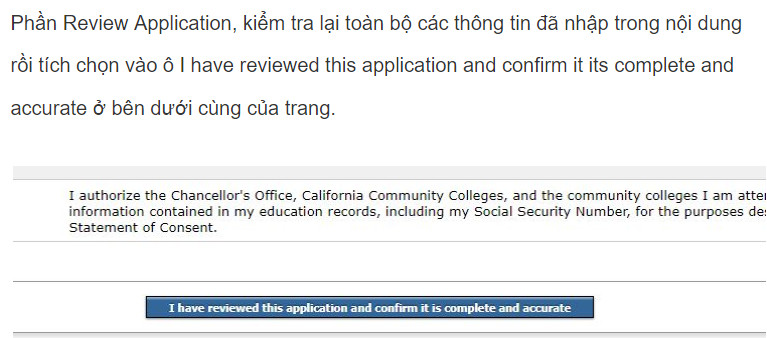
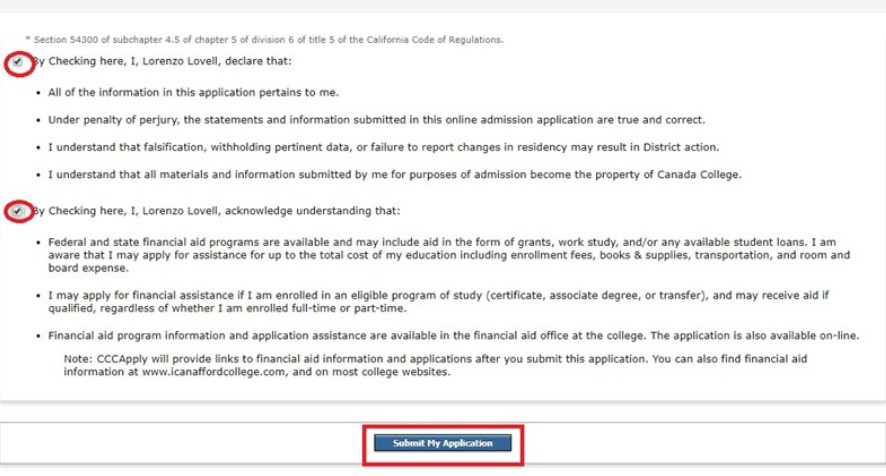
3. Nhận tài khoản Google Drive không giới hạnLúc nãy có phần điền Gmail đăng ký, mình bảo bạn điền Gmail hay dùng vào đó. Giờ bạn vào Gmail đó để nhận Email xác nhận. Email đầu tiên sẽ được gửi đến cho bạn. Tuy nhiên, bạn vẫn cần phải chờ thêm vài Email nữa để hoàn thành đăng ký Google Drive Unlimitted.Bạn nhận được Email đầu tiên thì khoản một đến hai tiếng sau sẽ nhận được cái thứ hai nhé. Sẽ có hai Email gửi tới chứa tài khoản và mật khẩu được cấp cho bạn. Bạn sẽ dùng nó để đăng nhập vào Google Drive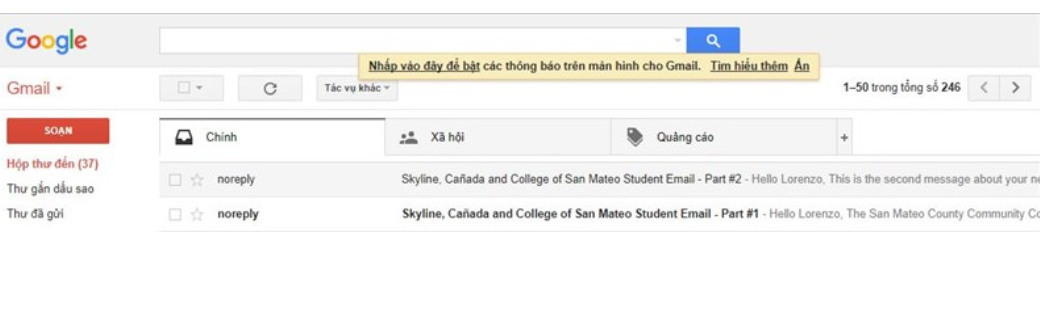
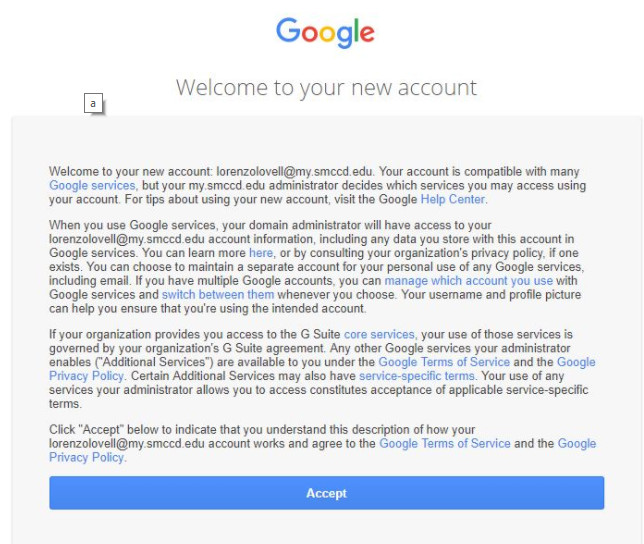
Sau khi đăng nhập thành công, bạn nên đổi mật khẩu ngay cho dễ nhớ.
- Passwords Are Still a Problem According to the 2019 Verizon Data Breach Investigations Report
It’s that time of year again! The time of year when all information security professionals eagerly devour the newly-released Verizon Data Breach Investigations Report (DBIR).Though the report is worth a read in its entirety, a few access and authentication-related findings especially stood out to us this year. The types of attacks and threat actions may evolve from year to year, but one thing has remained the same: supper cleaner Compromised passwords are still a leading contributor to successful attacks.A brief overview of the DBIRNow in its 12th year, the DBIR is often referred to as “required reading” for anyone working in the cybersecurity field. This comprehensive report analyzes security trends, explores how data breaches happen, and shares strategies for companies to improve security.As the report has grown in reach and significance, more cybersecurity companies have contributed data, giving us new and detailed insights into the threat landscape. The 2019 DBIR received contributions from 73 data sources and analyzed a total of 41,686 security incidents, of which 2,013 (~5%) were confirmed data breaches photo video vault.80% of hacking-related breaches still tied to passwordsYou’ve likely seen the statistic that 81% of data breaches are caused by compromised, weak, and reused passwords. That data point originated from the 2017 DBIR and has been widely cited since.The 2019 DBIR confirmed that not much has changed, with 80% of hacking-related breaches still involving compromised and weak credentials. 29% of all breaches, regardless of attack type, involved the use of stolen credentials.Even as we see more businesses investing in password management, it’s clear that there are many companies struggling to properly manage passwords and prevent password-related attacks.Password managers mentioned as a critical toolDon’t take our word for it on the importance of password management. The DBIR specifically mentions password managers as a key recommended tool in foiling hacking attempts. The report even uses the analogy of auditing and securing all your doors.“Static credentials are the keys,” says the DBIR. “Password managers and two-factor authentication are the spool pins in the lock. Don’t forget to audit where all your doors are. It doesn’t help to put XO-9’s on most of your entrances if you’ve got one in the back rocking a screen door.”We couldn’t agree more. Every password-protected account is essentially a doorway to your business.Multifactor authentication minimizes impact of stolen credentialsAs the above quote exemplifies, the report also repeatedly mentions the importance of multifactor authentication. By adding a second step to the authentication process and requiring additional ‘factors’ to prove a user’s identity, stolen credentials are no longer enough for attackers to gain access photo video vault.From the C-suite to the “front lines” employees, everyone in your organization is protecting valuable information, and every account they use should be treated with the appropriate care. Though education and training are important to raising employee awareness, putting effective tools in place – like a password manager and multifactor authentication – ensure that best practices are the default.Email accounts and web servers are hot targetsA popular attack this year involved using stolen credentials to compromise email accounts and web servers with the aim to steal money or sensitive data. Cloud-based mail servers were among the top assets affected in data breaches (~40%). Using stolen credentials to compromise an email account, an actor could launch large-scale phishing campaigns or send targeted emails to encourage bogus invoices and money transfers.Again, the report mentions that, “It is a good idea to deploy multiple factor authentication throughout all systems that support it and discourage password reuse. These actions will definitely help mitigate the impact of stolen credentials across the organization.” A password manager can reduce or eliminate password reuse while multifactor authentication can thwart attacks with stolen credentials. Both solutions are essential to a strong security posture.Now is the time to invest in stronger access management cleaner masterThis year’s report of course explores much more than what we’ve highlighted here. But for those businesses that have yet to invest in an access management strategy that includes password management and multifactor authentication, the 2019 DBIR makes a convincing case that it is an essential tool for reducing and preventing common attacks. Not only will an Enterprise Password Management solution like LastPass improve the overall security of your organization – especially when paired with multifactor authentication – you’ll also see a boost in productivity as employee password frustrations go down and IT can focus on more value-add activities.
- 5 Signs Your Email Was Hacked – and What to Do About It
In many ways, your email account is the digital equivalent of your house address. You give it to people and businesses, so they know where to send the products and helpful information you requested. It offers a way to keep in touch with family and friends smart cleaner.But email addresses have evolved to be so much more than just an inbox. When you sign up for something that requires an email address, you’re essentially using it as proof of your identity, too. And that means your email address becomes a very valuable target for attackers looking to find a way to steal personal information or even money.To better protect your email account, learn the signs of someone tampering with your inbox, take steps to correct any issues, and practice good security hygiene going forward.Here are some typical signs that someone is abusing your email account:1. A changed password.Perhaps the most obvious – and most panic-inducing – sign that your account may be hacked is that you can no longer log in with the same password. First, be sure you’re using the correct password (a password manager like LastPass ensures you’re using the right one). If login problems continue, initiate the password recovery photo vault process. If the recovery methods don’t work (either because the hackers have rerouted the recovery information or you don’t have access to your secondary recovery email or device) then your only option may be to get in touch with customer service.2. Strange emails in your sent folder.Not all attackers will completely takeover your account and lock you out. Sometimes, they just want to commandeer your account, either to send spam or to gather more information about you while trying to hide the activity from you.Check your sent folder to see if there are any messages you don’t remember sending, especially mass emails to your contacts. It’s possible that an attacker will have deleted any sent messages to cover their tracks, though, so it isn’t always possible to tell if something was sent without your knowledge3. Unexpected password reset emails.Keep an eye out for password reset emails that you don’t remember requesting. An attacker may be trying to find out which banks, shopping sites video vault, and other services you use. Be on the lookout for suspicious emails or calls claiming to be from your bank and asking for more information, like PIN codes or passwords.4. Complaints from contacts.If friends and family in your contacts list start emailing or messaging you to let you know they’re receiving strange content from you, this could be a sign someone is using your email inbox to send spam and phishing emails. It’s possible that someone is just spoofing your account, but if you’re receiving multiple reports from people in your address book, it’s much more likely that your account has been hacked.5. Unusual IP addresses, devices, and/or browsers.Many email services offer the ability to check your login activity and show the IP addresses or locations where your account has been accessed from. It may also show the browsers and/or devices used. If you see locations or devices you don’t recognize, it’s possible someone is tampering with your account.If you encounter one or more of the above signs that your account has been tampered with, there are several things you should do as soon as possible. Taking immediate action will hopefully minimize damage and prevent issues from happening again in the future.Change your passwordIf you suspect unauthorized access to your inbox, change your password immediately. Use LastPass to generate a new, unique password.If you’ve lost access to the account, try the recovery process. If it fails or doesn’t work, contact customer service as soon as possible.Add two-factor authenticationIf you weren’t using two-factor authentication before, now is the time to turn it on. Most email providers support the option for a second login step, which requires you to provide additional “factors” before access to the account is granted. Two-factor authentication is one of the most effective methods for delaying or preventing attacks.Set up a new accountSometimes, despite best efforts to regain access to the account, you’re not able to get back in. In that case, you’ll need to start the work of setting up a new email address and updating all your other accounts to use your new email address. If other accounts were affected by the hack, you’ll need to spend time recovering them, too.Alert friends and familyAttackers may use your email account to send spam or try to steal information from family and friends. Make sure your contacts are aware of what happened, so they can be on the lookout for suspicious emails or calls. If necessary, let contacts know of your new email address where they can reach you.Double-check account recovery informationIf you did regain access to the account, double-check your account recovery information. This means checking any email addresses that are listed as a recovery email address, and any phone numbers that are listed. If you don’t recognize the emails or phone numbers, change them immediately.Check account forwarding, autoreplies, etcAlso, check that there is no auto-forwarding or autoreplies enabled for your inbox that you didn’t set up yourself. Attackers may be using these options to get copies of emails sent to you or to automatically send spam to your contacts.Investigate additional security optionsLook into other security options from your email provider, or that are specific to your device. This could include security alerts when signing in from new locations or devices, or the option to remotely wipe devices or accounts if they’re lost secret calculator lock or stolen.Check if other accounts were affectedBecause your email is used to secure other accounts, it’s important to check if any were affected. Make sure you can log in, and consider changing the password to a new, generated password. If necessary, update the email address, too. Look into available security options like two-factor authentication and additional alerts.If you have trouble accessing any accounts, take immediate action to try resetting the password or contacting customer service.Run antivirus and clean up your deviceIt’s possible the attackers gained access through malware on your device. Be sure to run an antivirus scan to check for spyware, keyloggers, and other types of malware. Ensure your browsers and apps are up-to-date. Remove any third-party extensions or apps that you no longer need or use cleaner apps. If you’re not regularly backing up your files and programs, now is the time to start.Ask for helpIf you’re not sure about taking the above steps yourself, or run into additional problems, ask someone for help. Sometimes it pays to have a professional help you remediate the situation. Yes, this may require additional time (and cost), but preventing future security issues is well worth the initial investment.Dealing with a hacked email account can be a headache. Taking precautions to better protect your account now can help prevent or mitigate an attack. Educating yourself on what type of suspicious activity to look for can help you identify problems earlier and act immediately.
PR
コメント
プロフィール
HN:
No Name Ninja
性別:
非公開
最新記事
(09/13)
(08/28)
(08/28)
(08/27)
(08/27)